基于VTI隧道接口IPv4封装IPv6报文的IPSec实现
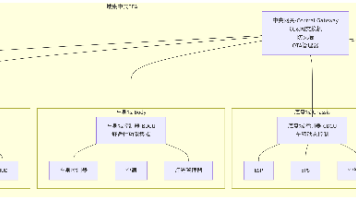
以下根据strongswan代码中的testing/tests/route-based/rw-shared-vti-ip6-in-ip4/中的测试环境,来看一下基于路由和VTI接口的IPv4封装IPv6报文的安全连接。拓扑结构如下:拓扑图中使用到的设备包括:虚拟主机carol和dave,以及虚拟网关moon。虚拟主机配置carol的配置文件:/etc/swanctl/swanctl.con...
以下根据strongswan代码中的testing/tests/route-based/rw-shared-vti-ip6-in-ip4/中的测试环境,来看一下基于路由和VTI接口的IPv4封装IPv6报文的安全连接。拓扑结构如下:
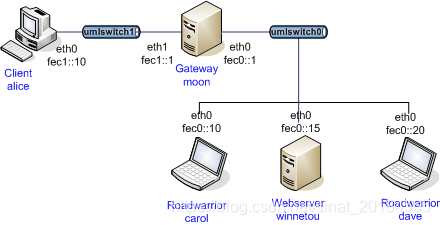
拓扑图中使用到的设备包括:虚拟主机carol和dave,以及虚拟网关moon。
虚拟主机配置
carol的配置文件:/etc/swanctl/swanctl.conf,内容如下。连接home中的字段vips设置为::,标识carol并不请求特定的虚拟IPv6地址。
connections {
home {
local_addrs = PH_IP_CAROL
remote_addrs = PH_IP_MOON
vips = ::
local {
auth = pubkey
certs = carolCert.pem
id = carol@strongswan.org
}
remote {
auth = pubkey
id = moon.strongswan.org
}
children {
home {
remote_ts = fec1::/16
updown = /usr/local/libexec/ipsec/_updown iptables
esp_proposals = aes128gcm128-x25519
}
}
version = 2
proposals = aes128-sha256-x25519
}
}
dave主机配置的配置与以上carol主机类似。
网关配置
moon网关的配置文件:/etc/swanctl/swanctl.conf,内容如下。其中为远程用户定义了虚拟地址池rw_pool,地址为IPv6网段fec3::/120。字段mark_in和mark_out等于42,其中mark_in指定在inbound方向的policies/SA所使用的Netfilter标记mark值;而mark_out指定在outbound方向上policies/SA设置的Netfilter标记mark值。此处未指定掩码值,即使用默认的0xffffffff。
connections {
rw {
local_addrs = PH_IP_MOON
pools = rw_pool
local {
auth = pubkey
certs = moonCert.pem
id = moon.strongswan.org
}
remote {
auth = pubkey
}
children {
net {
local_ts = fec1::/16
mark_in = 42
mark_out = 42
esp_proposals = aes128gcm128-x25519
}
}
version = 2
proposals = aes128-sha256-x25519
}
}
pools {
rw_pool {
addrs = fec3::/120
}
}
moon网关的配置文件:/etc/strongswan.conf,内容如下。其中install_routes等于0,表明不为IPSec子连接创建路由表项。
# /etc/strongswan.conf - strongSwan configuration file
swanctl {
load = pem pkcs1 x509 revocation constraints pubkey openssl random
}
charon-systemd {
load = random nonce aes sha1 sha2 pem pkcs1 curve25519 gmp x509 curl revocation hmac vici kernel-netlink socket-default updown
}
charon {
install_routes = 0
}
连接准备
操作流程如下,在两个远程虚拟主机carol和dave上,以及网关moon上启动strongswan进程。再者,在carol和dave上开启名称为home的子连接。前提是在moon网关上创建名称为vti0的vti虚拟接口,其key指定为42,意味着input和output方向的key值(ikey和okey)都指定为42。
另外,在moon网关的内部主机alice上配置到fec3::/16网段的下一跳路由fec1::1,即网关moon的eth1接口的IPv6地址。
alice::ip route add fec3::16 via fec1::1
moon::ip tunnel add vti0 local PH_IP_MOON remote 0.0.0.0 mode vti key 42
moon::sysctl -w net.ipv4.conf.vti0.disable_policy=1
moon::ip link set vti0 up
moon::ip route add fec3::16 dev vti0
moon::ip6tables -A FORWARD -i vti0 -j ACCEPT
moon::ip6tables -A FORWARD -o vti0 -j ACCEPT
以下在moon网关上使用ip tunnel命令查看创建的vti0接口,由于在IPSec连接建立之后,发送了两个ping报文,产生了统计信息:
moon:~# ip -s -d tunnel list
vti0: ip/ip remote any local 192.168.0.1 ttl inherit key 42
RX: Packets Bytes Errors CsumErrs OutOfSeq Mcasts
2 208 0 0 0 0
TX: Packets Bytes Errors DeadLoop NoRoute NoBufs
2 208 0 0 0 0
moon:~#
使用ip route命令添加目的网段10.3.0.0/28的报文经由vti0虚拟接口,以下为路由查看的输出。
moon:~# ip route
default via 192.168.0.254 dev eth0 onlink
10.1.0.0/16 dev eth1 proto kernel scope link src 10.1.0.1
10.3.0.0/28 dev vti0 scope link
192.168.0.0/24 dev eth0 proto kernel scope link src 192.168.0.1
moon:~#
vti0接口的disable_policy选项的使能,将导致接口相关的路由缓存设置DST_NOPOLICY标志(dst_entry->flags)。在策略检查函数xfrm_policy_check中,如果发现报文的路由缓存项设置了DST_NOPOLICY标志,将跳过策略检查。
ip6tables命令在filter表的FORWARD链中添加了如下的两条规则,允许进出vti0虚拟接口的所有IPv6流量。另外,可见在INPUT和OUTPUT两个链中,增加了运行ICMPv6类型为135和136的报文,即ICMPv6的邻居请求和邻居通告消息。
由于INPUT和OUTPUT链的默认策略为DROP,最后一条LOG规则用于记录被丢弃的报文,并且在INPUT链上记录的报文增加前缀" IN: “,在OUTPUT链上记录的报文增加前缀” OUT: "。
moon:~# ip6tables -L -n -v
Chain INPUT (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
2 144 ACCEPT icmpv6 * * ::/0 ::/0 ipv6-icmptype 135
2 128 ACCEPT icmpv6 * * ::/0 ::/0 ipv6-icmptype 136
0 0 LOG all * * ::/0 ::/0 LOG flags 0 level 4 prefix " IN: "
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
2 208 ACCEPT all vti0 * ::/0 ::/0
2 208 ACCEPT all * vti0 ::/0 ::/0
Chain OUTPUT (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
2 144 ACCEPT icmpv6 * * ::/0 ::/0 ipv6-icmptype 135
2 128 ACCEPT icmpv6 * * ::/0 ::/0 ipv6-icmptype 136
0 0 LOG all * * ::/0 ::/0 LOG flags 0 level 4 prefix " OUT: "
moon:~#
以下为在alice主机上ping一个不存在的IPv6地址,所产生的丢弃日志:
alice:~# ping6 fec3::99
moon:~# cat /var/log/kern.log
Nov 21 09:00:00 moon kernel: OUT: IN= OUT=eth1 SRC=fec1:0000:0000:0000:0000:0000:0000:0001 DST=fec1:0000:0000:0000:0000:0000:0000:0010 LEN=152 TC=0 HOPLIMIT=64 FLOWLBL=921304 PROTO=ICMPv6 TYPE=1 CODE=3 [SRC=fec1:0000:0000:0000:0000:0000:0000:0010 DST=fec3:0000:0000:0000:0000:0000:0000:0099 LEN=104 TC=0 HOPLIMIT=63 FLOWLBL=636582 PROTO=ICMPv6 TYPE=128 CODE=0 ID=2760 SEQ=1 ]
moon:~#
连接建立之后,carol和dave主机分别得到了虚拟IPv6地址:fec3::1 和 fec3::2, 如下moon网关上strongswan进程的日志记录。
moon charon-systemd: 05[IKE] peer requested virtual IP %any6
moon charon-systemd: 05[CFG] assigning new lease to 'carol@strongswan.org'
moon charon-systemd: 05[IKE] assigning virtual IP fec3::1 to peer 'carol@strongswan.org'
moon charon-systemd: 08[IKE] peer requested virtual IP %any6
moon charon-systemd: 08[CFG] assigning new lease to 'dave@strongswan.org'
moon charon-systemd: 08[IKE] assigning virtual IP fec3::2 to peer 'dave@strongswan.org'
数据流程
数据流程可参见: 中的介绍。以下为在carol主机上执行ping主机alice的操作,所产生的报文记录,从中也可看到ICMPv6的类型为135和136的Neighbour Solicitation和Advertisement报文。
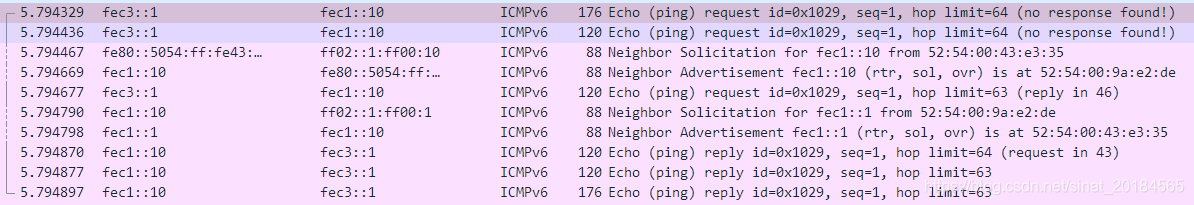
其中第一个ping请求报文如下,ICMPv6报文被封装在IPv4中。
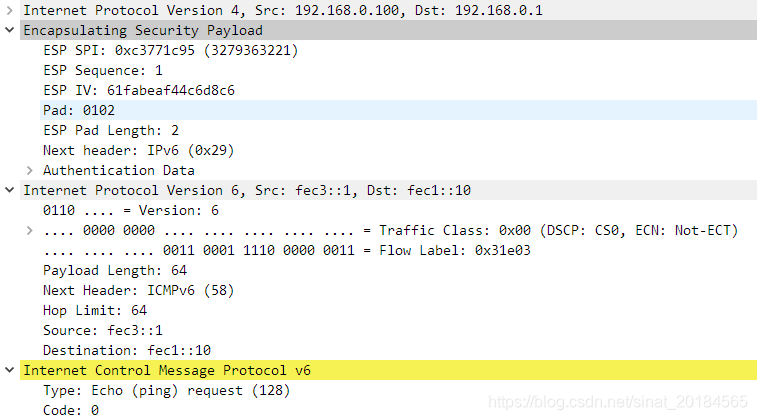
最后在moon网关上使用swanctl命令,可看到carol和dave的SA子连接信息在in/out两个方向上设置的mark值,mark-in=0x0000002a(42)和。mark-out=0000002a
moon:~# swanctl --list-sas --raw
list-sa event {rw {uniqueid=2 version=2 state=ESTABLISHED local-host=192.168.0.1 local-port=4500 local-id=moon.strongswan.org
remote-host=192.168.0.200 remote-port=4500 remote-id=dave@strongswan.org initiator-spi=3f7514ff8b1bda23 responder-spi=1becdb4811526141 encr-alg=AES_CBC encr-keysize=128 integ-alg=HMAC_SHA2_256_128 prf-alg=PRF_HMAC_SHA2_256 dh-group=CURVE_25519 established=2570 rekey-time=10997 remote-vips=[fec3::2] child-sas {net-2 {name=net uniqueid=2 reqid=2 state=INSTALLED mode=TUNNEL protocol=ESP spi-in=c5aa9c9e spi-out=cdf59e61
mark-in=0000002a mark-out=0000002a encr-alg=AES_GCM_16 encr-keysize=128 bytes-in=104 packets-in=1 use-in=2570 bytes-out=104 packets-out=1 use-out=2570 rekey-time=765 life-time=1390 install-time=2570 local-ts=[fec1::/16] remote-ts=[fec3::2/128]}}}}
list-sa event {rw {uniqueid=1 version=2 state=ESTABLISHED local-host=192.168.0.1 local-port=4500 local-id=moon.strongswan.org
remote-host=192.168.0.100 remote-port=4500 remote-id=carol@strongswan.org initiator-spi=9f42d8c7cccd4a58 responder-spi=dec45dec74068327 encr-alg=AES_CBC encr-keysize=128 integ-alg=HMAC_SHA2_256_128 prf-alg=PRF_HMAC_SHA2_256 dh-group=CURVE_25519 established=2570 rekey-time=11384 remote-vips=[fec3::1] child-sas {net-1 {name=net uniqueid=1 reqid=1 state=INSTALLED mode=TUNNEL protocol=ESP spi-in=c9c2ac4f spi-out=ce38ff75
mark-in=0000002a mark-out=0000002a encr-alg=AES_GCM_16 encr-keysize=128 bytes-in=624 packets-in=6 use-in=1006 bytes-out=624 packets-out=6 use-out=1006 rekey-time=959 life-time=1390 install-time=2570 local-ts=[fec1::/16] remote-ts=[fec3::1/128]}}}}
list-sas reply {}
No leaks detected, 1442 suppressed by whitelist
moon:~#
以及两个方向的安全策略中的mark/掩码值: mark 0x2a/0xffffffff。这次配置中mark值作为安全关联和策略查找匹配的一个重要参数,而路由到vti0虚拟接口的报文都被设置了相等的mark值。
moon:~# ip -s xfrm policy
src fec1::/16 dst fec3::2/128 uid 0
dir out action allow index 1129 priority 326271 ptype main share any flag (0x00000000)
mark 0x2a/0xffffffff
tmpl src 192.168.0.1 dst 192.168.0.200
proto esp spi 0xcdf59e61(3455426145) reqid 2(0x00000002) mode tunnel
level required share any
enc-mask ffffffff auth-mask ffffffff comp-mask ffffffff
src fec3::2/128 dst fec1::/16 uid 0
dir in action allow index 1112 priority 326271 ptype main share any flag (0x00000000)
mark 0x2a/0xffffffff
tmpl src 192.168.0.200 dst 192.168.0.1
proto esp spi 0x00000000(0) reqid 2(0x00000002) mode tunnel
level required share any
enc-mask ffffffff auth-mask ffffffff comp-mask ffffffff
src fec1::/16 dst fec3::1/128 uid 0
dir out action allow index 1105 priority 326271 ptype main share any flag (0x00000000)
mark 0x2a/0xffffffff
tmpl src 192.168.0.1 dst 192.168.0.100
proto esp spi 0xce38ff75(3459841909) reqid 1(0x00000001) mode tunnel
level required share any
enc-mask ffffffff auth-mask ffffffff comp-mask ffffffff
src fec3::1/128 dst fec1::/16 uid 0
dir in action allow index 1088 priority 326271 ptype main share any flag (0x00000000)
mark 0x2a/0xffffffff
tmpl src 192.168.0.100 dst 192.168.0.1
proto esp spi 0x00000000(0) reqid 1(0x00000001) mode tunnel
level required share any
enc-mask ffffffff auth-mask ffffffff comp-mask ffffffff
strongswan测试版本: 5.8.1
END
更多推荐
 已为社区贡献2条内容
已为社区贡献2条内容






所有评论(0)